The Difference Between Vulnerability Assessment And Penetration Testing
Vulnerability monitoring can be fed right into spot monitoring for reliable patching. Patches should be tested on a test system prior to rolling out to manufacturing. Safety and security controls & standards highlight the significance of susceptability scanning. For instance, The Facility for Web Safety And Security (CIS) Control # 3, "Continual Susceptability Monitoring," gets in touch with security professionals to "Constantly get, analyze, and do something about it on brand-new information in order to determine susceptabilities, remediate, and also reduce the window of chance for opponents."
It mentions that you require to "Run internal and external network vulnerability scans at the very least quarterly and after any kind of substantial change in the network." Both susceptability scanning and infiltration testing can feed right into the cyber threat evaluation process and help to identify controls best fit for the company, division or a technique.
It is really vital to understand the difference; each is essential and has different objectives and also results. Training is also important as supplying a device(s) to your safety and security team does not indicate that the atmosphere is safe. Absence of expertise being used a device(s) properly presents a larger protection danger.
Vulnerability Scanning Vs. Penetration Testing
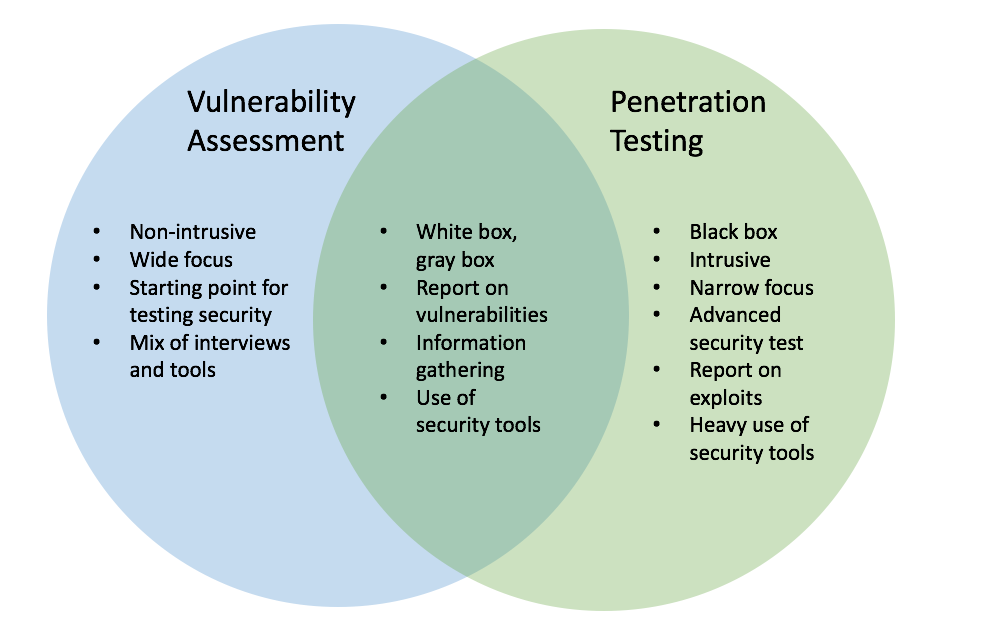
There seems to be a specific quantity of confusion within the Infotech sector regarding the distinctions between Penetration Screening and Susceptability Assessment. They are typically classified as the same point, when as a matter of fact they are not. Penetration Testing is more aggressive and intrusive, it goes an action additionally and also includes trying to practically break right into the client systems or web servers to confirm they are vulnerable.
The inherent threat is that an Infiltration Test, by potentially exploiting defects in the client software program or operating system, can trigger instability when screening manufacturing atmospheres. Nevertheless, if Penetration Screening is required, we carefully comprehend as well as consider all variables to stay clear of performance issues. An Infiltration Examination is an approach of reviewing the safety and security of a computer system or network by mimicing an attack by a harmful hacker.
This evaluation is accomplished from the placement of a potential assaulter and can entail active exploitation of safety and security susceptabilities. Any safety and security concerns that are found will exist to the system proprietor, together with an analysis of impact and generally with a proposal for mitigation or a technological solution.
Yet at the core, Susceptability Analyses entail the process of identifying and also quantifying technical vulnerabilities in a system, called exploits. These exploits placed the system in danger. In addition to common evaluations, Interactive Safety and security can meet the extra complicated needs of PCI-DSS ASV scanning.
Difference Between A Vulnerability Assessment And A Penetration Testing
When individuals misunderstand the differences in between infiltration screening and susceptability scans, they are typically missing an essential part in their overall network security profile and both are important for cybercrime avoidance. Susceptability scans as best rated Dallas IT services well as susceptability evaluations search systems for recognized susceptabilities. An infiltration examination tries to proactively make use of weak points in an environment.
Regular susceptability scanning is needed for preserving details protection. Secureworks case feedback (IR) experts have observed some clients performing vulnerability scans regular as well as others not performing these essential scans in any way. Secureworks analysts suggest scanning every new tool before it is released as well as at the very least quarterly afterwards. Any type of modifications to the tools ought to promptly be followed by an additional susceptability scan.
Organizations ought to keep standard reports on essential equipment and ought to examine modifications in open ports or included services. A vulnerability scanner (e. g., Nessus, GFI LANGuard, Rapid7, Retina, Qualys) can notify network defenders when unapproved modifications are made to the environment. Resolving detected changes against change-control records can aid figure out if the modification was authorized or if there is an issue such as a malware infection or an employee breaking change-control policies.
Transmission of unencrypted passwords, password reuse, as well as neglected data sources keeping legitimate customer qualifications are examples of issues that can be uncovered by a penetration examination. Penetration examinations do not need to be carried out as typically as vulnerability scans but should be duplicated often. Infiltration tests are best carried out by a third-party supplier as opposed to interior personnel to provide an objective view of the network atmosphere as well as avoid conflicts of passion.
Pentesting Vs Vulnerability Scanning: What's The Difference?
The tester should have a breadth and depth of experience in info modern technology, ideally in the company's location of organization; an ability to believe abstractly and attempt to expect danger star behaviors; the focus to be thorough and detailed; and a desire to reveal how and why a company's atmosphere might be jeopardized.
It can have appendices noting certain details, however the major body of the record need to focus on what data was endangered as well as just how. To be valuable for the consumer, the report should explain the real approach of strike and make use of, the worth of the exploited information, and also referrals for enhancing the company's safety and security pose.
Susceptability scanning and penetration testing are both crucial to a detailed safety and security method. They are effective devices to monitor as well as enhance an organization's network setting.